Threat Name: Dridex
File Download Locations:
These files may no longer be active, but please use caution when downloading as they are malicious.
7sumur.com/73/20.exe
baypipo.com/55/55.exe
cellsitemanagement.com/73/20.exe
chiokings.com/88/15.exe
crestliquors.com/73/20.exe
croningroup.com/73/20.exe
dalmatian-bizhub.com/55/55.exe
deborah-abesser.com/88/15.exe
elkettasandassociates.com/25/10.exe
empreinte.com.ar/42/91.exe
footingclub.com/85/20.exe
hoinghihoithao.com/88/15.exe
jenisgroup.com/88/15.exe
joyofcamping.com/88/15.exe
kang-ning.com/353/654.exe
kapagrup.com/94/053.exe
m-bikes.gr.193-92-97-57.linuxzone26.grserver.gr/42/91.exe
mercury.powerweave.com/85/20.exe
mindfullivingprograms.com/73/20.exe
njgems.com/55/55.exe
orenkaholidays.com/5/0.exe
revistacannicas.com.ar/42/91.exe
seedsindaphne.org/85/20.exe
segurosdenotebooks.com.br/25/10.exe
thepattersonco.com/85/20.exe
tpsci.com/88/15.exe
tvteachervideos.com/42/91.exe
yubido.web.fc2.com/5/0.exe
zolghadri-co.com/25/10.exe
File Names:
The file names are numerical and 1 through 3 digits long.
0.exe
053.exe
10.exe
15.exe
20.exe
55.exe
654.exe
91.exe
IP Connections:
The malware will attempt to make CONNECT requests to the below IP addresses and ports.
144.76.238.214:4443
185.12.94.48:7443
185.12.95.191:4443
188.120.249.231:8443
70.32.74.108:7443
78.24.218.186:8443
78.46.60.131:4443
94.242.58.146:4443
Regex Query:
The following regex query should find the HTTP URI and file name of the executable file. Since the directory and file names are pretty consistent in the fact that they have been numerical values so far, it should be pretty easy to locate in your logs.
- \/[1-9]{1,3}\/[0-9]{1,3}\.exe
The following Wireshark display filter (using regex) should also work:
- http.request.uri matches "\/[1-9]{1,3}\/[0-9]{1,3}\.exe"
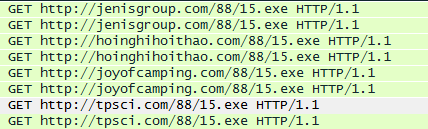
You should see similar information below in the Info column in Wireshark when you run the above query:
I am sure that I will be adding more indicators for this malware soon as it has been pretty prevalent over the past few weeks. Thanks for reading.
No comments:
Post a Comment
Please feel free to leave a comment that is relevant to the post.